vRNI Notes – Moving a group of App VMs + Associated FW Rules from VMC to VMC
A few months ago, my colleague Tom Zukowski demo’ed the vRealize Network Insight and HCX Fling to a group of internal employees and he mentioned there was an ability to also export the existing firewall rules associated with a vRNI application group and import them into VMC. This perked my interest because customers have been asking for an end to end migration tool for workloads. HCX does a phenomenal job of moving the workloads in every fashion possible. The one thing it does not do is import or create firewall rules related to the group of vm’s being moved.
My goal was to prove and demonstrate that we could use vRNI to define an application or a group of vm’s that will move via HCX AND transplant the associated application firewall rules at the destination. The outcome would be an entire application moved to the cloud with security in place. You would not have to manually recreate every firewall rule, service group, inventory group, and IP to group assignment at the destination.
It took us several weeks as we had day jobs but we were able to complete the task. Below are my rough notes.
Order of steps is important.
Source:
VMC SDDC
M20/vSphere 8/NSX-T 4.01
3 Tier App Running: Web,App,DB
vRNI installed as OVA
Destination:
VMC SDDC
M18v5/vSphere 7.0.3/NSX-T 3.1.5
Prep:
HCX Established between both SDDC’s
vRNI Appliance installed in Source SDDC
3 Tier App running in source SDDC
vRNI Toolkit Fling Appliance running in source SDDC
vRNI-rule-import-vmc-nsxt Python script located at destination SDDC
Basic Overview Steps:
- Establish HCX between source and destination SDDC’s.
- Install vRNI OVA and configure with source vCenter.
- Use vRNI to define application group.
- Install vRNI Toolkit Fling Appliance.
- Use vRNI Toolkit Fling Appliance to export Application Group into an HCX Mobility Group in source SDDC HCX instance.
- Export associated Application Group VM’s Firewall Rules from vRNI into XML file.
- At destination SDDC, use Windows VM with vRNI Application Group VM’s Firewall Rule XML file and vRNI Firewall Python Rule script and run it against the destination VMC/NSX-T. *Script must have access to private NSX-T Manager interface of SDDC.
- Use HCX to move Application Group VM’s to destination SDDC.
- You will now have moved the VM and their associated FW rules, groups, services into VMC.
Step by Step:
#1 – Establish HCX between source and destination SDDC’s.
*I am assuming you know how to configure HCX, configure firewall rules to allow HCX access, etc.
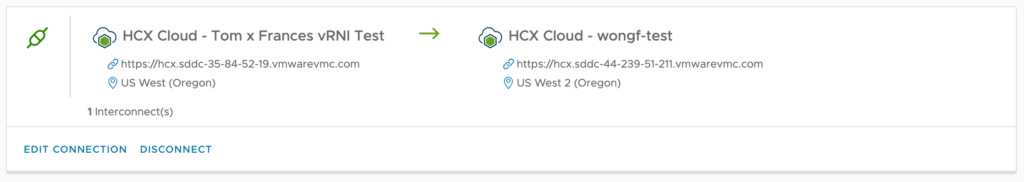
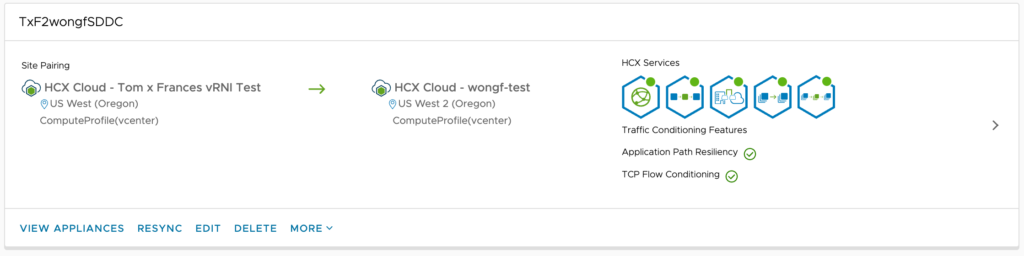
#2 – Install vRNI OVA and configure with source vCenter.
https://www.vmware.com/products/vrealize-network-insight.html
You will need either the vRealize Network Insight OVA or use the vRealize Network Insight Cloud edition.
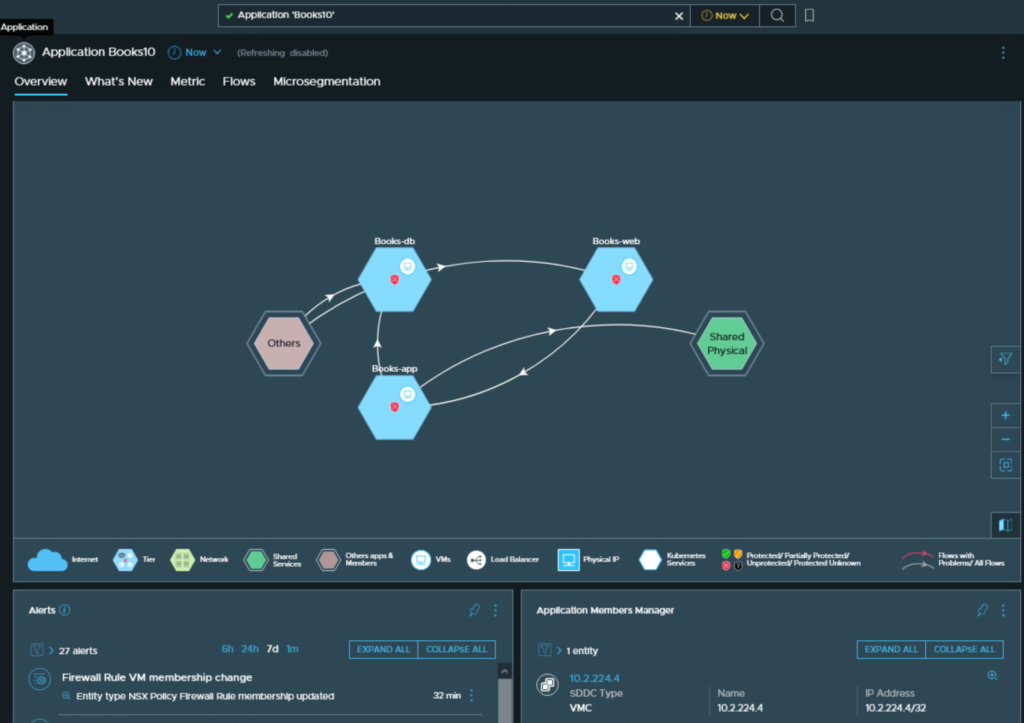
#3 -Use vRNI to define application group.
How to create Applications in vRNI – https://docs.vmware.com/en/VMware-vRealize-Network-Insight/Cloud/com.vmware.vrni.using.doc/GUID-C998FBF3-1293-46D4-B9C4-F5C6CB66B0F8.html
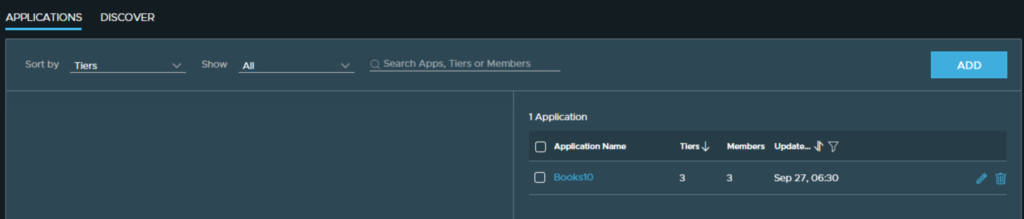
#4 – Install vRNI Fling Appliance in the source SDDC & configure.
vRealize Network Insight Toolkit – https://flings.vmware.com/vrealize-network-insight-toolkit
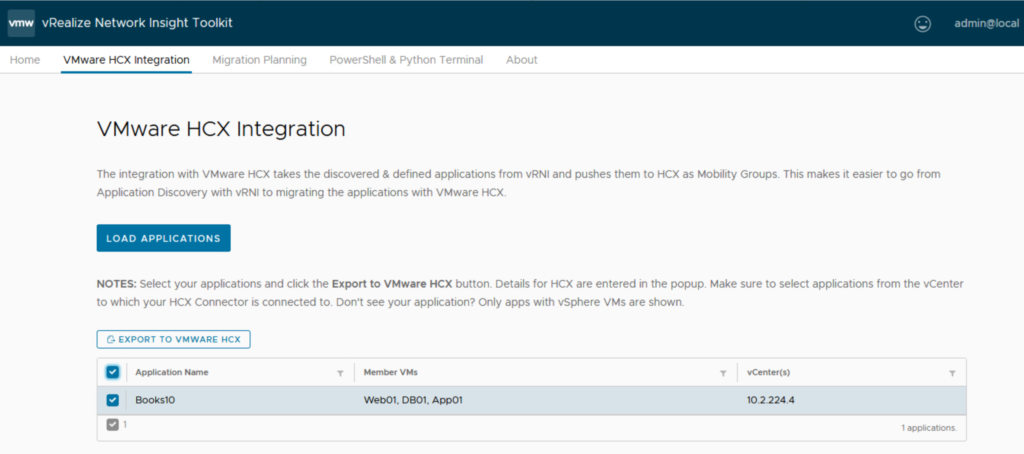
#5 – Use vRNI Fling Appliance to export Application Group into an HCX Mobility Group in source SDDC HCX instance.
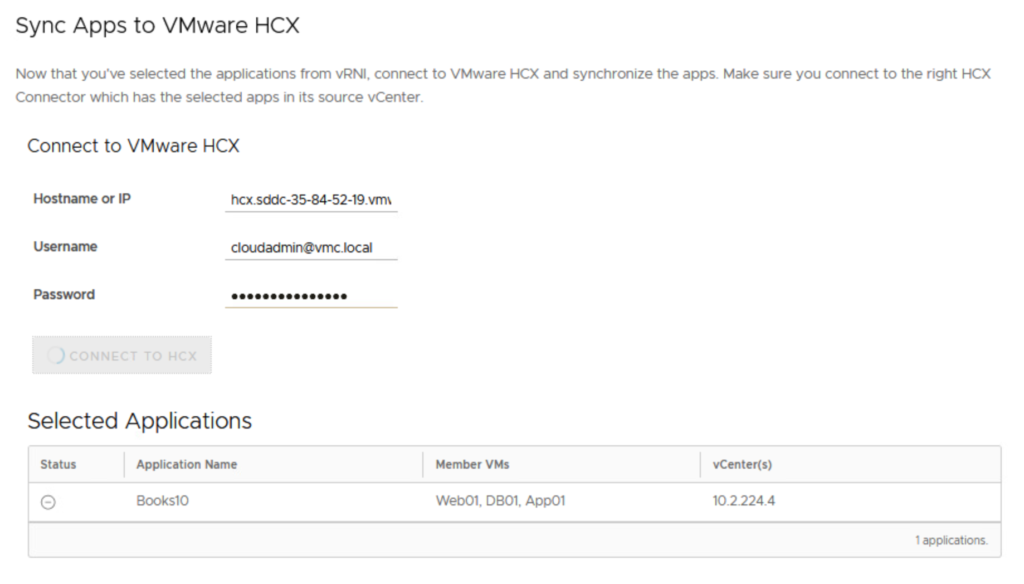
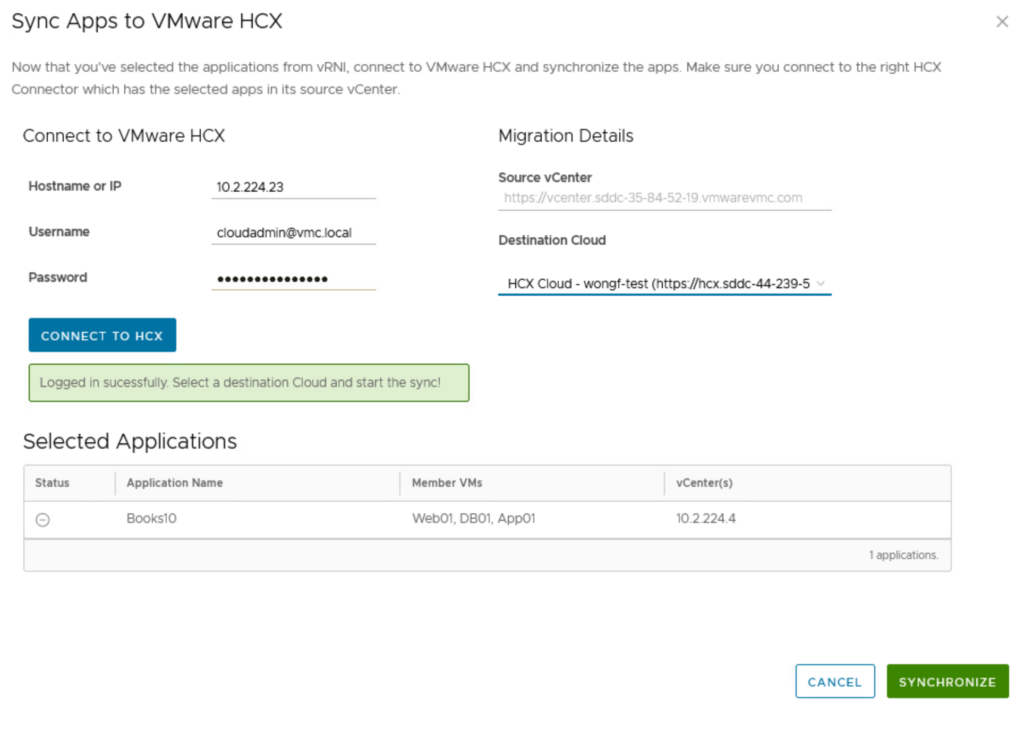
Once you hit Synchronize, the interface is a little odd and it may look like it’s stuck when it’s done.
Look at HCX Migration screen to see the Mobility Groups created.
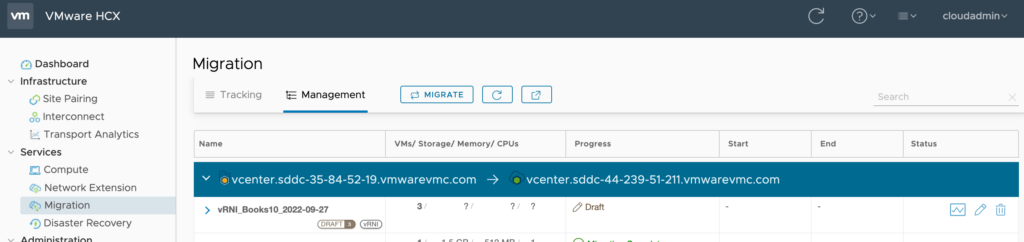
#6 – Export associated Application Group VM’s Firewall Rules from vRNI into XML file.
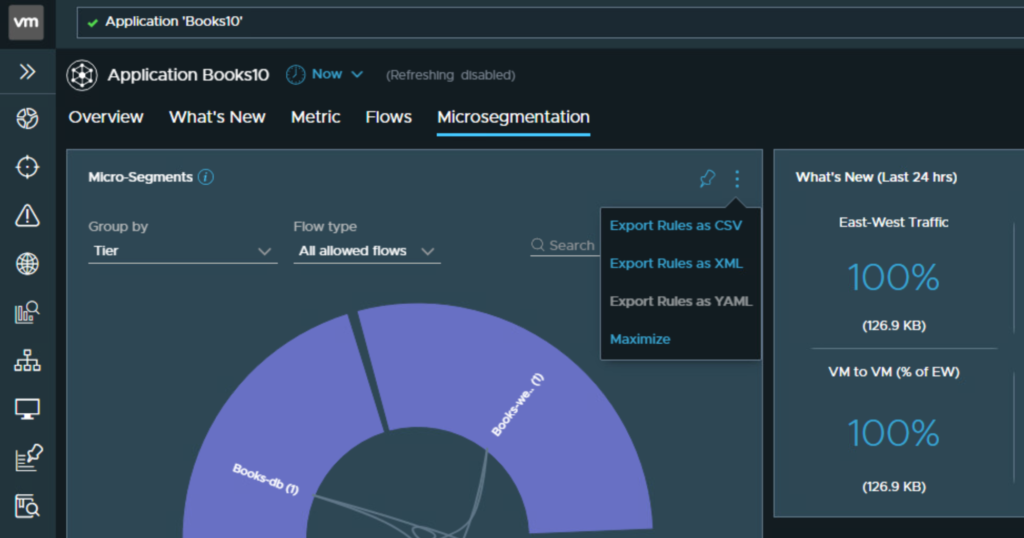
From vRNI, locate and open defined application group.
Select Microsegmentation.
Click on 3 dots in the Micro Segments widget and select Export Rules as XML.
#7 – At destination SDDC, use a Windows VM with vRNI Application Group VM’s Firewall Rule XML file and vRNI Firewall Python Rule script and run it against the destination VMC/NSX-T.
vRealize Network Insight Rule Import VMC NSX-T Script – https://github.com/vrealize-network-insight/vrni-rule-import-vmc-nsxt
*Script must have access to private NSX-T Manager interface of SDDC.
*Enable firewalls between compute and mgmt segments. Recommend not using default compute segment. Create and use a new Compute segment.
*You must have the following information: VMC Org ID, SDDC ID, Refresh Token, full folder location for firewall rules generated from vRNI and the exported group member file.
*Within a windows desktop, install python script requirements.
***Note – script DOES NOT CREATE the segments at the destination. You will need to recreate those segments either through the UI, through the NSX API, or through a script. See the SDDC Import/Export Fling for more information. I recommend doing this BEFORE you run the import script.
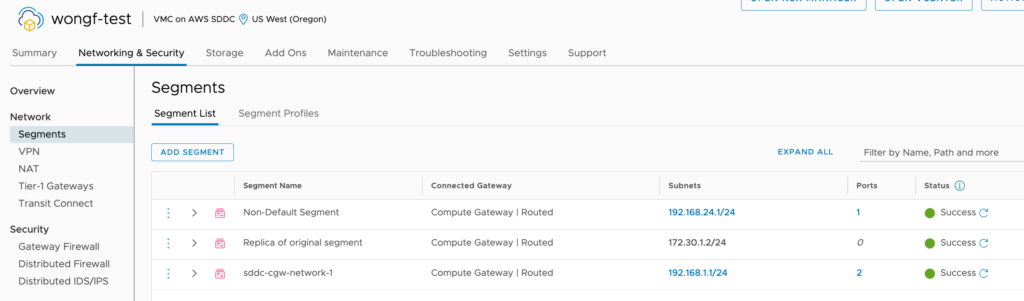
Run the script.
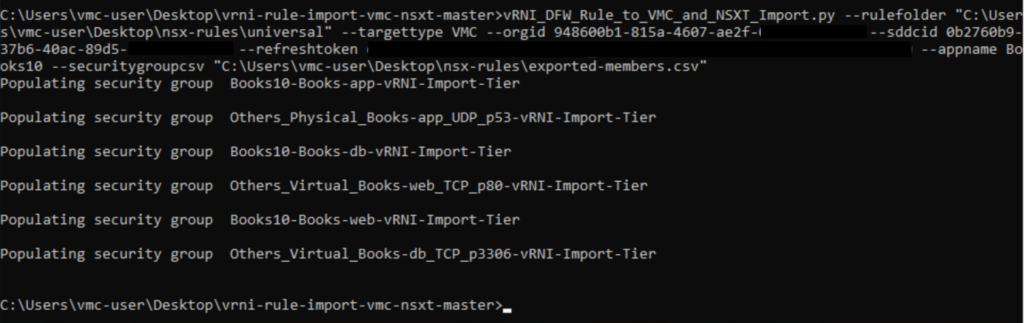
*I opted to leave the firewall rules disabled. You can enable them upon import.
******
Reference
I spent a fair amount of time messing around with the commands so I’m including my rough notes so you know exactly what the command is.
You will need to collect the below pieces of information to include in your command line.
You do not need to feed it all in at once but it made things a lot easier for me.
The python script will prompt you for the information but seriously, the strings are so long that it sucks to cut and paste back and forth but you do you.
| Commandline Options | My input |
| –rulefolder RULEFOLDER | c:\Users\vmc-user\Desktop\nsx-rules\universal |
| –orgid ORGID | ab9671bc-9bc8-45b8-bb6d-xxxxxxxxxxxx |
| –sddcid SDDCID | 0b2760b9-37b6-40ac-89d5-xxxxxxxxxxxx |
| –refreshtoken REFRESHTOKEN | You must generate a user token from the VMware CSP portal with rights to VMC |
| –appname APPNAME | Books10 |
| –securitygroupcsv Exported-members.csv File Location | c:\users\vmc-user\desktop\nsx-rules\exported-members.csv |
Command on Windows:
vRNI_DFW_Rule_to_VMC_and_NSXT_Import.py –targettype VMC –rulefolder “c:\Users\vmc-user\Desktop\nsx-rules\universal” –orgid ab9671bc-9bc8-45b8-bb6d-xxxxxxxxxxxx –sddcid 0b2760b9-37b6-40ac-89d5-xxxxxxxxxxxx –refreshtoken xxx –appname Books10 –securitygroupcsv “c:\users\vmc-user\desktop\nsx-rules\exported-members.csv”
******
Look for the new objects in your destination SDDC.
The DFW FW rules created
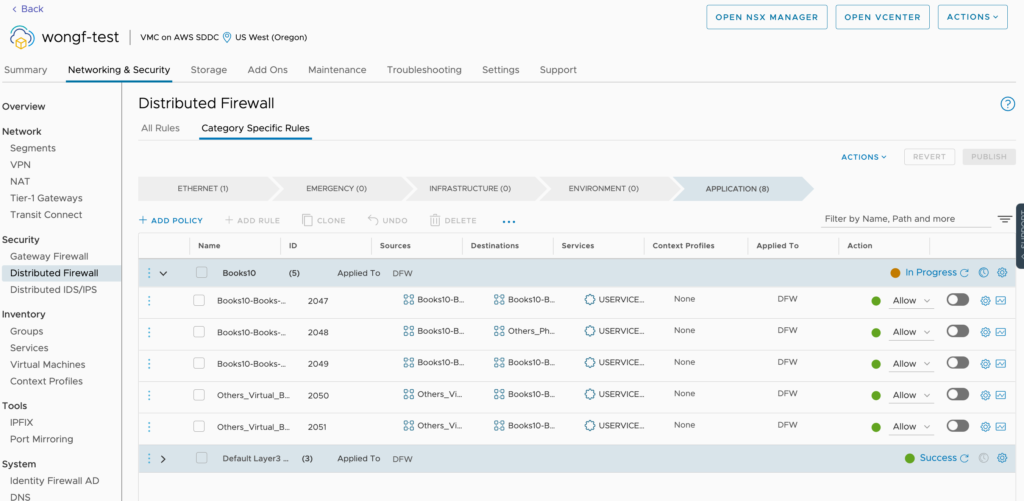
A closer look at the DFW Rules
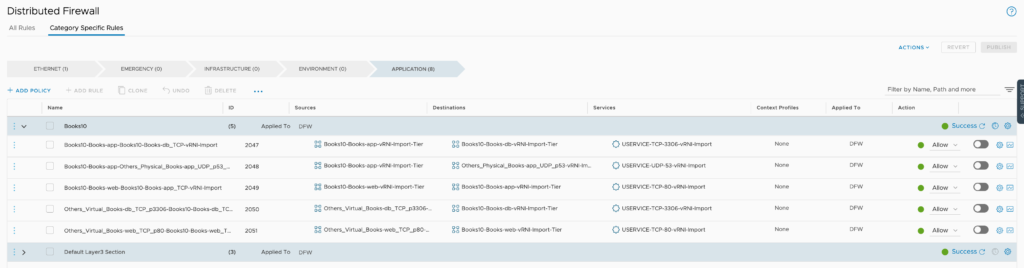
The newly created NSX Groups
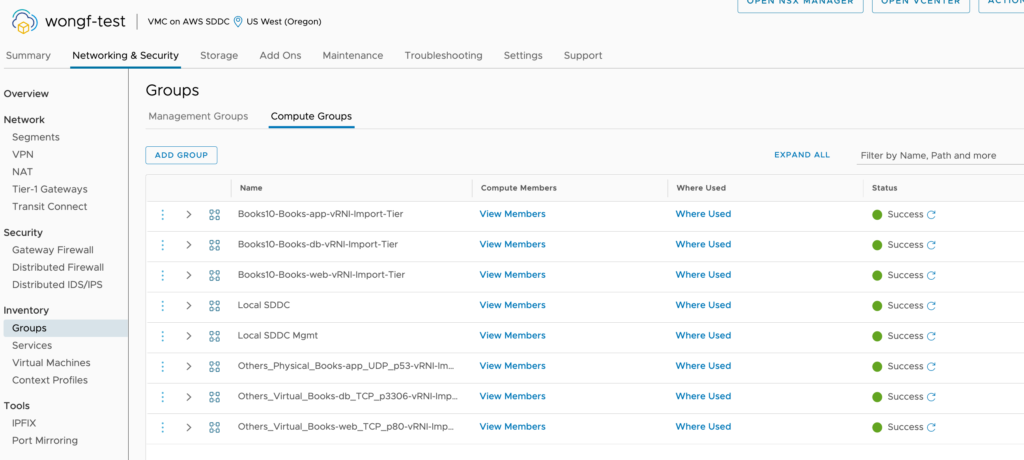
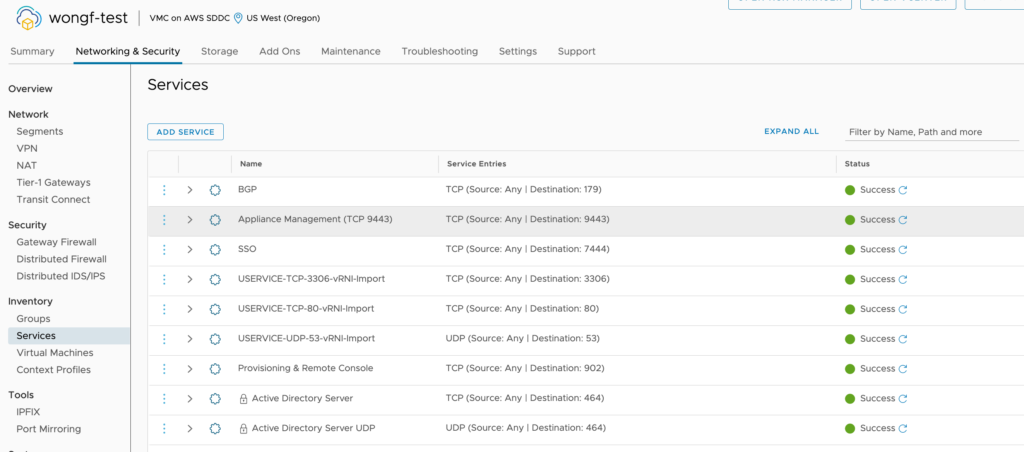
The newly created services related to the app
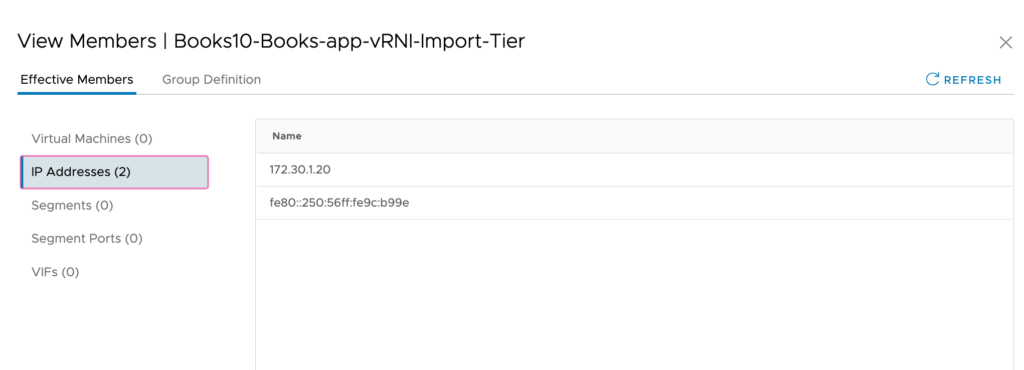
A closer look at a group created with the IP’s intact.
#8 – Use HCX to move Application Group VM’s to destination SDDC.
You must edit the group and kick off the HCX migration.
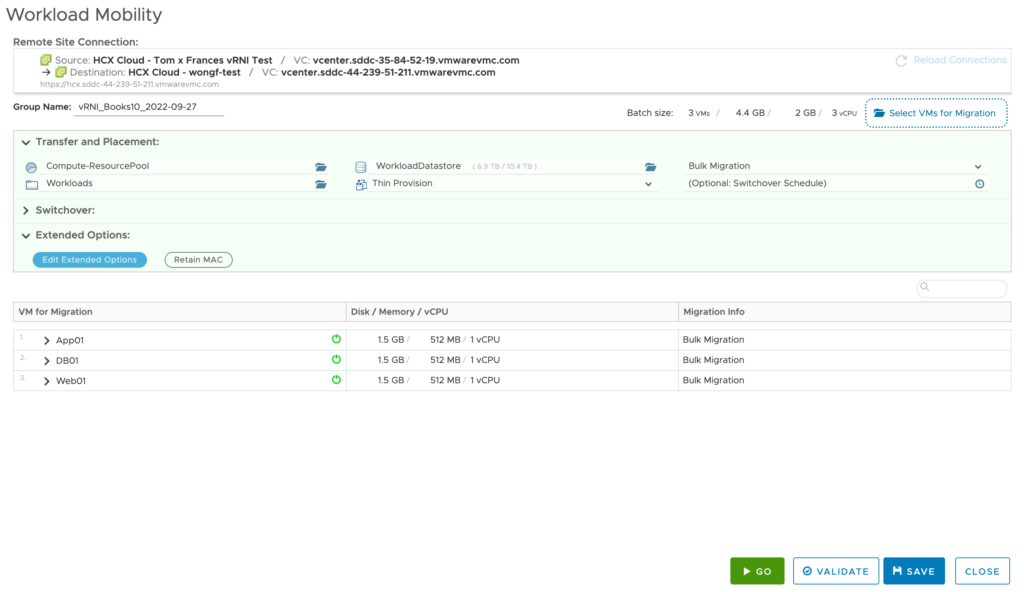
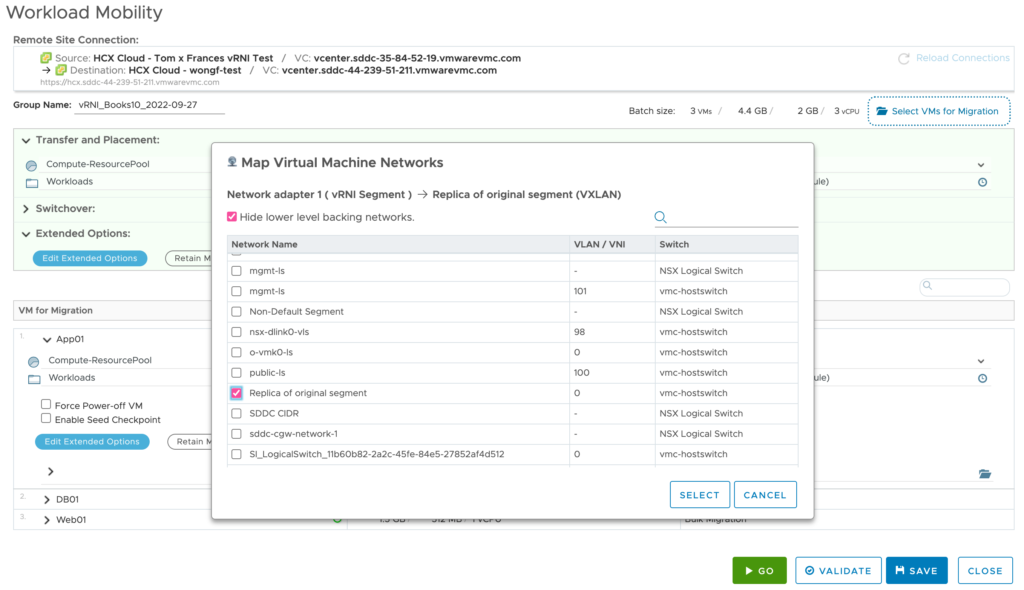
*You must select the destination network. In this example, I am not using an extended network.
*I am also performing a Bulk Migration, not a vMotion.
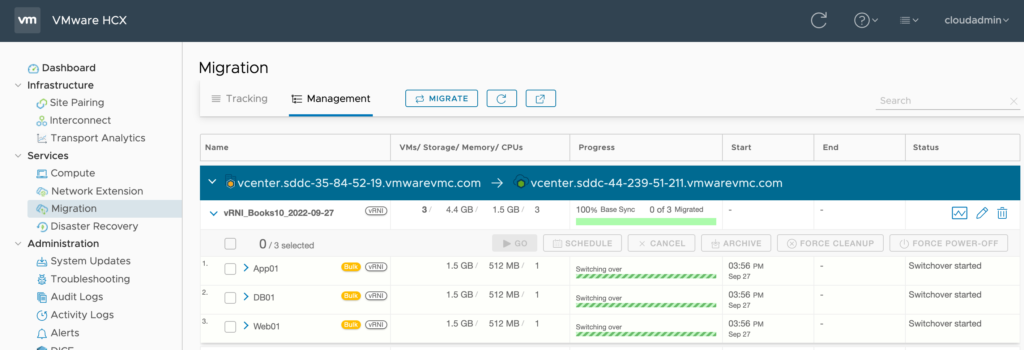
#9 – Completed HCX Migration
Entire app stack now running at destination with original IP’s.
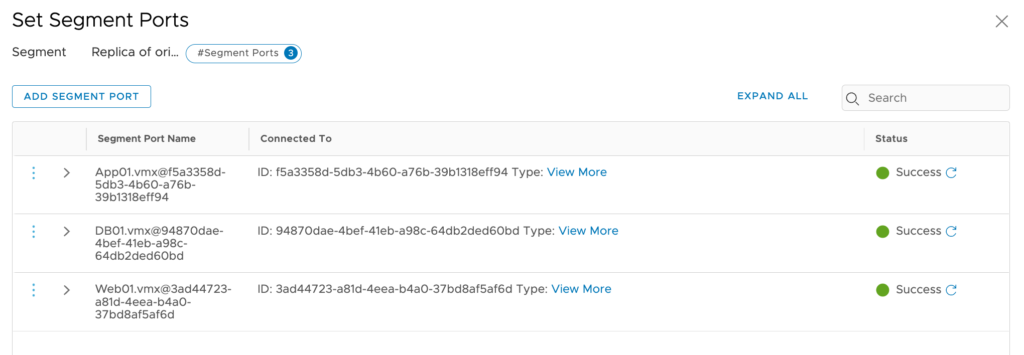
The replica segment now shows the new vm’s connected
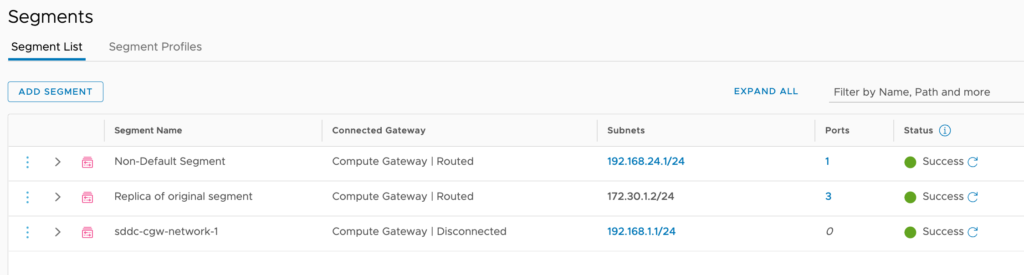
A closer look at the ports connected on the replica segment
You will now have moved the VMs and their associated FW rules, groups, services into VMC. Not only that but you have moved from an open network security model to one where specific firewall rules are created ONLY from the network flows that were previously generated between these app servers. You can now move forward to a zero trust networking model if you so choose.
As always, test until satisfied. This is not currently supported by VMware as the vRNI Appliance Fling and the associated Python scripts are community generated.
It’s obvious that I glossed over the amount of work it took to stand this up and I skipped a lot of the details like making sure you have vCenter access, a working Windows VM inside the SDDC, etc. This post assumes vSphere, VMware Cloud on AWS, Windows, HCX, commandline, firewall, and NSX construct experience.
A big thank you to Tom Z. who worked with me in our extra hour here and there as we stood up a full environment in order to do this. And Martijn Smit to whom we owe a lot of thanks for developing the python scripts that provided this functionality.
I’m just a user but the vision is real – we CAN take entire applications, move them to VMC, AND plant the associated network security in the cloud. It takes some prep work but it works!
Good Luck!
1 thought on “Automating VM Migration AND their Firewall rules to VMC”
Comments are closed.